| Oracle® Database Vault Administrator's Guide 11g Release 1 (11.1) Part Number B31222-01 |
|
|
View PDF |
| Oracle® Database Vault Administrator's Guide 11g Release 1 (11.1) Part Number B31222-01 |
|
|
View PDF |
This chapter describes how to configure secure application roles. It includes the following sections:
In Oracle Database Vault, you can create a secure application role that you enable with an Oracle Database Vault rule set. Regular Oracle Database secure application roles are enabled by custom PL/SQL procedures. You use secure application roles to prevent users from accessing data from outside an application. This forces users to work within the framework of the application privileges that have been granted to the role.
The advantage of basing database access for a role on a rule set is that you can store database security policies in one central place, as opposed to storing them in all your applications. Basing the role on a rule set provides a consistent and flexible method to enforce the security policies that the role provides. In this way, if you must update the security policy for the application role, you do it in one place, the rule set. Furthermore, no matter how the user connects to the database, the result is the same, because the rule set is bound to the role.
You can run reports on secure application roles that you create in Oracle Database Vault. See "Related Reports" for more information.
This chapter explains how to configure secure application roles by using Oracle Database Vault Administrator. To configure secure application roles by using the PL/SQL interfaces and packages provided by Oracle Database Vault, refer to the following appendixes:
Log in to Oracle Database Vault Administrator using a database account that has been granted the DV_OWNER role.
At a minimum, you must have the DV_ADMIN role. "Starting Oracle Database Vault Administrator" explains how to log in.
In the Administration page, under Database Vault Feature Administration, click Secure Application Roles.
In the Secure Application Roles page:
To create a new secure application role, click Create.
To edit an existing secure application role, select it from the list and then click Edit.
Remember that you can modify an existing secure application role only if it has been created in Oracle Database Vault. You cannot modify secure application roles or database roles that have been created outside of Oracle Database Vault. If you want to modify an existing Oracle Database role so that it can work with Oracle Database Vault, create a new secure application role in Oracle Database Vault and then grant the existing role to the secure application role. For example, in SQL*Plus:
SQL> GRANT myExistingDBrole TO myDVrole;
After you create a new secure application role, you must modify your code to use this new role. You can use DVSYS.DBMS_MACSEC_ROLES.SET_ROLE in your application code to accomplish this. See "SET_ROLE Function" for more information about the SET_ROLE function.
In the Create (or Edit) Role page, enter the following settings and then click OK.
General
Enter the following settings:
Role: Enter the name using no more than 30 characters, with no spaces. Preferably, enter the role name in upper case letters, though you are not required to do so. Ensure that this name follows the standard Oracle naming conventions for role creation using the CREATE ROLE statement, described in Oracle Database SQL Language Reference. This attribute is mandatory.
Status: Select either Enabled or Disabled to enable or disable the secure application role during run time. The default is Enabled. This attribute is mandatory.
Enabled: Calls the DVSYS.DBMS_MACSEC_ROLES.SET_ROLE function to determine whether or not a role is set for a database session.
See "SET_ROLE Function" for more information about this function.
Disabled: Prevents the need for the DVSYS.DBMS_MACSEC_ROLES.SET_ROLE function.
See "Oracle Database Vault PL/SQL Packages" for more information about the DVSYS.DBMS_MACSEC_ROLES.SET_ROLE function.
Rule Set
From the list, select the rule set that you want to associate with the secure application role. This attribute is mandatory.
When calling DVSYS.DBMS_MACSEC_ROLES.SET_ROLE, if the rule set evaluates to true, then Oracle Database Vault sets the role for the database session. If the rule set evaluates to false, then the role is not set.
See Chapter 5, "Configuring Rule Sets" for more information about rule sets.
Users who have database administrative privileges can use the DROP ROLE command to delete secure application roles that were created using Oracle Database Vault.
To prevent the database administrator from deleting a secure application role, when you create secure application roles, protect them by using a realm. To do so, add the role to a realm authorization. See "Defining Realm Authorization" for more information.
Before you delete a secure application role, you can locate the various references to it by querying the role-related Oracle Database Vault views. See "Oracle Database Vault Public Views" for more information.
To delete a secure application role:
Check and modify any applications that may be using the secure application role that you want to delete.
In the Oracle Database Vault Administration page, select Secure Application Roles.
In the Secure Application Roles page, select the role that you want to remove.
Click Remove.
In the Confirmation page, click Yes.
The process flow for a secure application role that is managed by Oracle Database Vault is as follows:
Create or update the role either in Oracle Database Vault Administrator or by using the secure application role-specific functions in the DVSYS.DBMS_MACADM package.
See "Secure Application Role Functions Within DVSYS.DBMS_MACADM" for more information.
Modify your application to call the role, by using the DVSYS.DBMS_MACSEC_ROLES.SET_ROLE function.
See "SET_ROLE Function" for more information.
Oracle Database Vault then evaluates the rule set associated with the secure application role.
If the rule set evaluates to true, then Oracle Database Vault enables the role for the current session. If the rule set evaluates to false, the role is not enabled. In either case, Oracle Database Vault processes the associated auditing and custom event handlers for the rule set associated with the secure application role.
Suppose you wanted to create a secure application role to allow employees to manage their own accounts within the in-house applications your company has created. To do so, you would follow these steps:
Step 1: Create a Rule Set to Be Used with the Secure Application Role
Step 2: Create the Secure Application Role Using the Rule Set
You can use an existing rule set or create a new one. See Chapter 5, "Configuring Rule Sets" for information about creating a new rule set. Oracle Database Vault provides a set of default rule sets that you can use.
Figure 8-1 shows how to create a secure application role for employees to manage their own accounts.
Figure 8-1 Secure Application Role Example
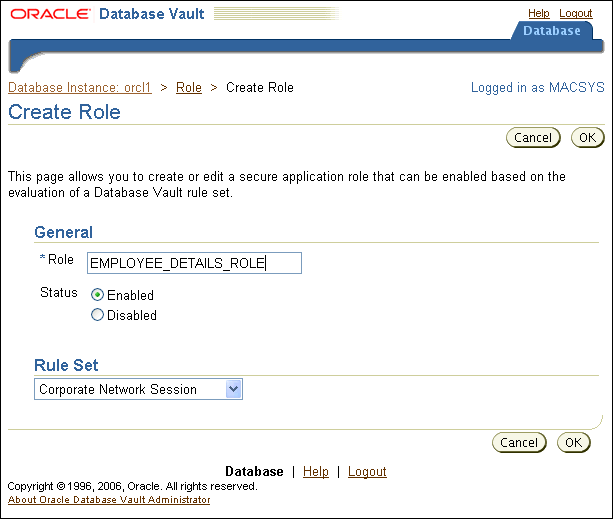
Next, connect as a database administrator who can grant the SELECT privilege and is a realm owner of the realm protecting the object. Grant SELECT privileges for the data to the employee_details_role as follows.
SQL> CONNECT appadmin
Enter password: password
Connected.
SQL> GRANT SELECT ON hr.employees TO employee_details_role;
Grant succeeded.
After the secure application role has been created, applications or database sessions can enable it by calling the DVSYS.DBMS_MACSEC_ROLES.SET_ROLE function:
DVSYS.DBMS_MACSEC_ROLES.SET_ROLE('employee_details_role')
Now, with these settings in place, a powerful system administrator can be prevented from remotely accessing any sensitive employee data, such as the salary for file clerk Ida Neau. Here is what happens when the system administrator tries this from the office:
SQL> CONNECT system@hrdb_from_cubicle
Enter password: password
Connected.
SQL> select dvf.f$network from dual
CORPORATE
SQL> EXEC DVSYS.DBMS_MACSEC_ROLES.SET_ROLE('employee_details_role');
PL/SQL procedure successfully completed.
SQL> SELECT count(*) from hr.employees
COUNT(*)
----------
57
----------
But here is what happens when the administrator tries to set the employee_details_role role from home:
SQL> CONNECT system@hrdb_from_home
Enter password: password
Connected.
SQL> select dvf.f$network from dual
REMOTE
SQL> EXEC DVSYS.DBMS_MACSEC_ROLES.SET_ROLE('employee_details_role');
*
ERROR at line 1:
ORA-01031: insufficient privileges
As you can see, the security protection in this example happens at the time the administrator tries to set the SET_ROLE call—not when he or she attempts data access. Had the administrator first tried accessing the data in HR.EMPLOYEES, the same thing would happen: the security protection in place would prevent data access.
You can check system performance by running tools such as Oracle Enterprise Manager (including Oracle Enterprise Manager Database Control, which is installed by default with Oracle Database), Statspack, and TKPROF. For more information about Oracle Enterprise Manager, see the Oracle Enterprise Manager documentation set. For information about Database Control, refer to its online Help. Oracle Database Performance Tuning Guide describes the Statspack and TKPROF utilities.
Table 8-1 lists Oracle Database Vault reports that are useful for analyzing secure application roles. See Chapter 11, "Oracle Database Vault Reports" for information about how to run these reports.
Table 8-1 Reports Related to Secure Application Roles
| Report | Purpose |
|---|---|
|
"Secure Application Role Audit Report" |
To find audit records generated by the Oracle Database Vault secure application role-enabling operation. To generate this type of audit record, enable auditing for the rule set associated with the role. |
|
"Secure Application Configuration Issues Report" |
To find secure application roles that have nonexistent database roles, or incomplete or disabled rule sets |
|
"Rule Set Configuration Issues Report" |
To find rule sets that have no rules defined or enabled, which may affect the secure application roles that use them |
|
"Powerful Database Accounts and Roles Reports" |
To find information about powerful database accounts and roles |