| Oracle® Database Vault Administrator's Guide 11g Release 1 (11.1) Part Number B31222-01 |
|
|
View PDF |
| Oracle® Database Vault Administrator's Guide 11g Release 1 (11.1) Part Number B31222-01 |
|
|
View PDF |
This chapter provides a quick introduction to using Oracle Database Vault. You will learn how to start Oracle Database Vault Administrator, and then explore the basics of using Oracle Database Vault by creating a simple security configuration.
This chapter includes the following sections:
This section describes how to start Oracle Database Vault Administrator.
Tip:
If you are using Oracle Enterprise Manager Database Control, you can configure it for an SSL (HTTPS) secure connection. For more information, see Oracle Enterprise Manager Advanced Configuration in Oracle Enterprise Manager 10g Release 10.1. To access this manual, visit Oracle Technology Network (OTN) athttp://www.oracle.com/technology/index.html
Follow these steps:
From the Documentation menu, select Enterprise Manager.
On the Oracle Enterprise Manager 10g Release Documentation page, under Other Releases, select the Oracle Enterprise Manager Release 1 (10.1) Documentation link.
On the Oracle Enterprise Manager 10g Release 1 (10.1) Documentation page, select either PDF or HTML for Oracle Enterprise Manager Advanced Configuration, whose part number is B12013-03.
In Chapter 4, "Enterprise Manager Security," go to "Configuring Security for the Database Control."
To start Oracle Database Vault Administrator:
From a browser, enter the following URL:
https://host_name:port/dva
In this specification:
host_name: The server where you installed Oracle Database Vault
port: The Oracle Enterprise Manager Console HTTP port number
For example:
https://myserver:1158/dva
If you are unsure of the port number, open the ORACLE_HOME/host_sid/sysman/config/emd.properties file and search for REPOSITORY_URL.
If you cannot start Oracle Database Vault Administrator, check that the Oracle database console process is running.
On UNIX systems: Navigate to the $ORACLE_HOME/bin directory and run the following command:
./emctl status dbconsole
If you must start the dbconsole process, then run the following command:
./emctl start dbconsole
On Windows systems: In the Administrative Services, select the Services utility, and then right-click the OracleDBConsolesid service. If necessary, select Start from the menu to start the database console.
Log files are in the following directory:
$ORACLE_HOME/sysman/log
Log in by using the Oracle Database Vault Owner account that you created during installation.
By default, you cannot log in to Oracle Database Vault Administrator by using the SYS, SYSTEM, or other administrative accounts. You can log in if you have the DV_ADMIN or DV_OWNER roles.
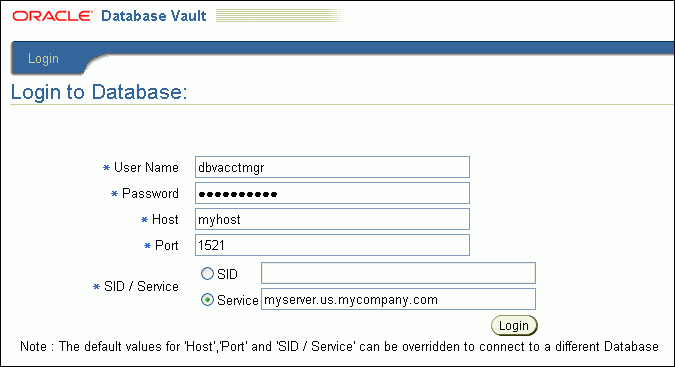
By default, the login page enables you to log in to the default Oracle Database Vault installation. If you want to log in to a different Database Vault installation, enter the following values:
Host: Enter the host name of the computer of the Oracle Database Vault installation you want.
Port: Enter the port number.
SID/Service: To connect using the server identification, select SID and then enter the server ID of the database you want, for example, orcl. To connect using the service information, select Service, and then enter the service identification in the following format:
server.domain
For example:
myserver.us.mycompany.com
To find the SID and service connection information, check the tnsnames.ora file. By default, this file is located in ORACLE_BASE/ORACLE_HOME/network/admin.
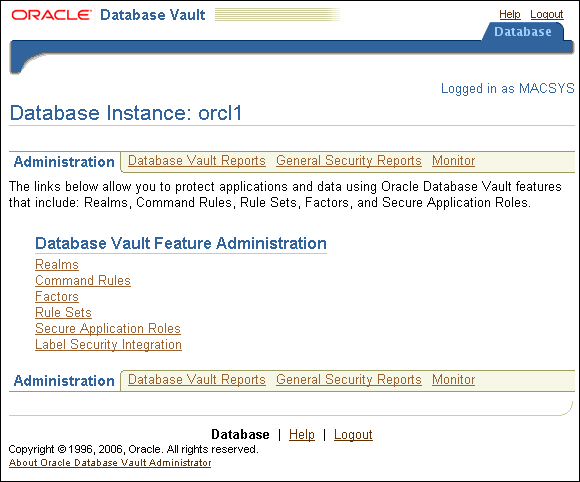
Figure 3-1 shows the Oracle Database Vault Administrator home page, which appears after you log in.
Figure 3-1 Oracle Database Vault Administrator Home Page
In this tutorial, you will create a simple security configuration for the HR sample database schema. In the HR schema, the EMPLOYEES table has information such as salaries that should be hidden from most employees in the company, including those with administrative access. To accomplish this, you will add the HR schema to the secured objects of the protection zone, which in Oracle Database Vault is called a realm, inside the database. Then you grant limited authorizations to this realm. Afterward, you will test the realm to make sure it has been properly secured. And finally, to see how Oracle Database Vault provides an audit trail on suspicious activities like the one you will try when you test the realm, you will run a report.
Before you can use this tutorial, ensure that the HR sample schema is installed. See Oracle Database Sample Schemas for information on installing the sample schemas.
You will follow these steps:
In this tutorial, the SYSTEM user will grant ANY privileges to a new user account, SEBASTIAN. In order to do this, SYSTEM will need to be included in the Oracle Data Dictionary realm.
To include SYSTEM in the Oracle Data Dictionary realm:
Log in to Oracle Database Vault Administrator using a database account that has been granted the DV_OWNER role.
"Starting Oracle Database Vault Administrator" explains how to log in.
In the Administration page of Oracle Database Vault Administrator, under Database Vault Feature Administration, click Realms.
In the Realms page, select Oracle Data Dictionary from the list and then click Edit.
In the Edit Realm: Oracle Data Dictionary page, under Realm Authorizations, click Create.
In the Create Realm Authorization Page, from the Grantee list, select SYSTEM [USER].
For Authorization Type, select Owner.
Leave Authorization Rule Set at <Non Selected>.
Click OK.
In the Edit Realm: Oracle Data Dictionary page, SYSTEM should be listed as an owner under the Realm Authorizations.
Click OK to return to the Realms page.
To return to the Administration page, click the Database Instance instance_name link over Realms.
Log in to SQL*Plus with administrative privileges and access the HR schema. You will log on using the SYSTEM account.
$ sqlplus system
Enter password: password
SQL> SELECT FIRST_NAME, LAST_NAME, SALARY FROM HR.EMPLOYEES WHERE ROWNUM < 10;
FIRST_NAME LAST_NAME SALARY
-------------------- ------------------------- ----------
Donald OConnell 2600
Douglas Grant 2600
Jennifer Whalen 4400
Michael Hartstein 13000
Pat Fay 6000
Susan Mavris 6500
Hermann Baer 10000
Shelley Higgins 12000
William Gietz 8300
9 rows selected.
As you can see, SYSTEM has access to the salary information in the EMPLOYEES table of the HR schema. This is because SYSTEM is automatically granted the DBA role, which includes the SELECT ANY TABLE system privilege.
Realms can protect one or more schemas, individual schema objects, and database roles. Once you create a realm, you can create security restrictions that apply to the schemas and their schema objects within the realm. Your first step is to create a realm for the HR schema.
Follow these steps:
If you have not done so already, return to the Administration page by clicking the Database Instance instance_name link over Realms.
In the Administration page, under Database Vault Feature Administration, click Realms.
In the Realms page, click Create.
In the Create Realm page, under General, enter HR Realm after Name.
After Status, ensure that Enabled is selected so that the realm can be used.
Under Audit Options, ensure that Audit On Failure is selected so that you can create an audit trial later on.
Click OK.
The Realms Summary page appears, with HR Realm in the list of realms.
At this stage, you are ready to add the EMPLOYEES table in the HR schema to the secured objects of the HR realm.
Follow these steps:
In the Realms page, select HR Realm from the list and then click Edit.
In the Edit Realm: HR Realm page, scroll to Realm Secured Objects and then click Create.
In the Create Realm Secured Object page, enter the following settings:
Object Owner: Select HR from the list.
Object Type: Select %.
Object Name: Enter EMPLOYEES.
Click OK.
In the Edit Realm: HR Realm page, click OK.
At this stage, there are no database accounts or roles authorized to access or otherwise manipulate the database objects the realm will protect. So, the next step is to authorize database accounts or database roles so that they can have access to the schemas within the realm. You will create the SEBASTIAN user account. After you authorize him for the realm, SEBASTIAN will be able to view and modify the EMPLOYEES table.
First, in SQL*Plus, create a user account that has the SELECT privilege on the EMPLOYEES table in the HR schema. To do so, log in SQL*Plus using an account that has the DV_ACCTMGR role, which is used for account management. When you installed Oracle Database Vault, the account that you created during the installation process was granted the DV_ACCTMGR role. For example, suppose you had created an account called DBVACCTMGR during the installation process. You would log in using the DBVACCTMGR account, and then create the user account as follows:
SQL> CONNECT dbvacctmgr Enter password: password SQL> CREATE USER SEBASTIAN IDENTIFIED BY seb_456987; User created. SQL> GRANT CONNECT TO SEBASTIAN; Grant succeeded. SQL> CONNECT SYSTEM Enter password: password Connected. SQL> GRANT SELECT ANY TABLE TO SEBASTIAN; Grant succeeded.
(Do not exit SQL*Plus; you will need it for Step 6: Test the Realm, when you test the realm.)
At this point SEBASTIAN still can query the EMPLOYEES table, because the GRANT statement overrides realm protection. If the GRANT statement were generic, for example, SELECT ANY TABLE, then Oracle Database Vault restricts access to all tables protected by realm, including HR.EMPLOYEES.
Next, authorize user SEBASTIAN to have access to the HR Realm as follows:
In the Realms page, select the HR Realm in the list of realms, and then click Edit.
In the Edit Realm: HR Realm page, scroll down to Realm Authorizations and then click Create.
In the Create Realm Authorization page, under Grantee, select SEBASTIAN from the list.
If SEBASTIAN does not appear in the list, select the Refresh button in your browser.
SEBASTIAN will be the only user who will have access to the EMPLOYEES table in the HR schema.
Under Authorization Type, select Owner.
The Owner authorization allows the user SEBASTIAN in the HR realm to manage the database roles protected by HR, as well as create, access, and manipulate objects within the realm. In this case, the HR user and SEBASTIAN will be the only persons allowed to view the EMPLOYEES table.
Under Authorization Rule Set, select <Not Assigned>, because rule sets are not needed to govern this realm.
Click OK.
To test the realm, try accessing the EMPLOYEES table as a user other than HR. The SYSTEM account normally has access to all objects in the HR schema, but now that you have safeguarded the EMPLOYEES table with Oracle Database Vault, this is no longer the case.
Log in to SQL*Plus as SYSTEM, and then try accessing the salary information in the EMPLOYEES table again:
sqlplus system
Enter password: password
SQL> SELECT FIRST_NAME, LAST_NAME, SALARY FROM HR.EMPLOYEES WHERE ROWNUM <10;
Error at line 1:
ORA-01031: insufficient privileges
As you can see, SYSTEM no longer has access to the salary information in the EMPLOYEES table.
However, user SEBASTIAN does have access to the salary information in the EMPLOYEES table:
SQL> CONNECT SEBASTIAN Enter password: seb_456987 Connected. SQL> SELECT FIRST_NAME, LAST_NAME, SALARY FROM HR.EMPLOYEES WHERE ROWNUM <10; FIRST_NAME LAST_NAME SALARY -------------------- ------------------------- ---------- Donald OConnell 2600 Douglas Grant 2600 Jennifer Whalen 4400 Michael Hartstein 13000 Pat Fay 6000 Susan Mavris 6500 Hermann Baer 10000 Shelley Higgins 12000 William Gietz 8300 9 rows selected.
Because you enabled auditing on failure for the HR Realm, you can generate a report to find any security violations such as the one you attempted in Step 6: Test the Realm.
Follow these steps:
In the Oracle Database Vault Administrator home page, click Database Vault Reports.
To run the report, log in using an account that has the DV_OWNER, DV_ADMIN, or DV_SECANALYST role. Note that user SEBASTIAN cannot run the report, even if it affects his own realm. "Oracle Database Vault Roles" describes these roles in detail.
In the Database Vault Reports page, scroll down to Database Vault Auditing Reports and select Realm Audit.
Click Run Report.
Oracle Database Vault generates a report listing the type of violation (in this case, the SELECT statement entered in the previous section), when and where it occurred, the login account who tried the violation, and what the violation was.
Follow these steps:
Remove the SYSTEM account from the Data Dictionary Realm.
Ensure that you are logged on to Oracle Database Vault Administrator using a database account that has been granted the DV_OWNER role.
From the Administration page, select Realms.
From the list of realms, select Oracle Data Dictionary, and then click Edit.
Under Realm Authorizations, select SYSTEM.
Click Remove, and in the Confirmation window, click Yes.
Delete the HR Realm.
In the Realms page, select HR Realm from the list of realms.
Click Remove, and in the Confirmation window, click Yes.
Drop user SEBASTIAN.
In SQL*Plus, log on as the Oracle Database Vault account manager (for example, DBVACCTMGR) you created when you installed Oracle Database Vault, and then drop SEBASTIAN as follows:
sqlplus dbvacctmgr
Enter password: password
SQL> DROP USER SEBASTIAN;
User dropped.