| Oracle® Security Overview 10g Release 1 (10.1) Part Number B10777-01 |
|
|
View PDF |
| Oracle® Security Overview 10g Release 1 (10.1) Part Number B10777-01 |
|
|
View PDF |
This chapter presents an overview of data security requirements and examines the full spectrum of data security risks that must be countered. It then provides a matrix relating security risks to the kinds of technology now available to protect your data. This chapter contains the following sections:
|
Note: As far as possible, this overview of security technology attempts to present issues independent of the way the technology is implemented. In some instances, however, a technology may only be provided by products from Oracle Corporation. In such cases, the conceptual discussion is from the point of view of the Oracle solution. Refer to Chapter 9, "Oracle Security Products and Features" for a complete discussion of security solutions available from Oracle Corporation. |
The field of data security is rife with mistaken beliefs that cause people to design ineffective security solutions. Here are some of the most prevalent security myths:
In fact, 80% of data loss is to caused by insiders.
In fact, encryption is only one approach to securing data. Security also requires access control, data integrity, system availability, and auditing.
In fact, 40% of Internet break-ins occur in spite of a firewall being in place.
To design a security solution that truly protects your data, you must understand the security requirements relevant to your site, and the scope of current threats to your data.
In an Internet environment, the risks to valuable and sensitive data are greater than ever before. Figure 1-1 presents an overview of the complex computing environment that your data security plan must encompass.
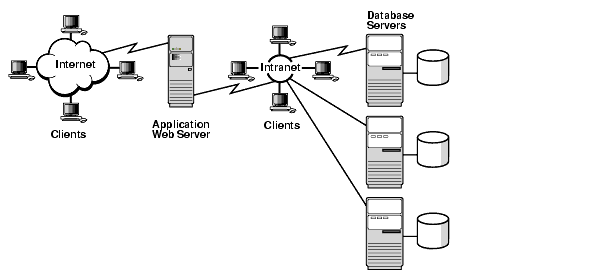
Text description of the illustration net81104.gif
You must protect databases and the servers on which they reside; you must administer and protect the rights of internal database users; and you must guarantee the confidentiality of ecommerce customers as they access your database. With the Internet continually growing, the threat to data traveling over the network increases exponentially.
To protect all the elements of complex computing systems, you must address security issues in many dimensions, as outlined in Table 1-1:
Think carefully about the specific security risks to your data, and make sure the solutions you adopt actually fit the problems. In some instances, a technical solution may be inappropriate. For example, employees must occasionally leave their desks. A technical solution cannot solve this physical problem: the work environment must be secure.
The following sections describe the basic security standards that technology must ensure:
A secure system ensures the confidentiality of data. This means that it allows individuals to see only the data that they are supposed to see. Confidentiality has several different aspects, discussed in these sections:
How can you ensure the privacy of data communications? Privacy is a very broad concept. For the individual, it involves the ability to control the spread of confidential information such as health, employment, and credit records. In the business world, privacy may involve trade secrets, proprietary information about products and processes, competitive analyses, as well as marketing and sales plans. For governments, privacy involves such issues as the ability to collect and analyze demographic information, while protecting the confidentiality of millions of individual citizens. It also involves the ability to keep secrets that affect the country's interests.
How can you ensure that data remains private, once it has been collected? Once confidential data has been entered, its integrity and privacy must be protected on the databases and servers where it resides.
How can you designate the persons and organizations who have the right to see data? Authentication is a way of implementing decisions about whom to trust. Authentication methods seek to guarantee the identity of system users: that a person is who he says he is, and not an impostor.
How much data should a particular user see? Access control is the ability to cordon off portions of the database, so that access to the data does not become an all-or-nothing proposition. A clerk in the Human Relations department might need some access to the emp table--but he should not be permitted to access salary information for the entire company. The granularity of access control is the degree to which data access can be differentiated for particular tables, views, rows, and columns of a database.
Note the distinction between authentication, authorization, and access control. Authentication is the process by which a user's identity is checked. When a user is authenticated, he is verified as an authorized user of an application. Authorization is the process by which the user's privileges are ascertained. Access control is the process by which the user's access to physical data in the application is limited, based on his privileges. These are critical issues in distributed systems. For example, if JAUSTEN is trying to access the database, authentication would identify her as a a valid user. Authorization would verify her right to connect to the database with Product Manager privileges. Access control would enforce the Product Manager privileges upon her user session.
A secure system ensures that the data it contains is valid. Data integrity means that data is protected from deletion and corruption, both while it resides within the database, and while it is being transmitted over the network. Integrity has several aspects:
A secure system makes data available to authorized users, without delay. Denial-of-service attacks are attempts to block authorized users' ability to access and use the system when needed. System availability has a number of aspects:
The Internet environment expands the realm of data security in several ways, as discussed in these sections:
Information is the cornerstone of e-business. The Internet allows businesses to use information more effectively, by allowing customers, suppliers, employees, and partners to get access to the business information they need, when they need it. Customers can use the Web to place orders that can be fulfilled more quickly and with less error, suppliers and fulfillment houses can be engaged as orders are placed, reducing or eliminating the need for inventory, and employees can obtain timely information about business operations. The Internet also makes possible new, innovative pricing mechanisms, such as online competitive bidding for suppliers, and online auctions for customers. These Internet-enabled services all translate to reduced cost: there is less overhead, greater economies of scale, and increased efficiency. The greatest promise of e-business is more timely, more valuable information accessible to more people, at reduced cost of information access.
The promise of e-business is offset by the security challenges associated with the disintermediation of data access. Cutting out the middleman--removing the distributors, wholesalers and retailers from the trading chain--too often cuts out the information security the middleman provides. Likewise, the user community expands from a small group of known, reliable users accessing data from the intranet, to thousands of users accessing data from the Internet. Application hosting providers and exchanges offer especially stringent--and sometimes contradictory--requirements of security by user and by customer, while allowing secure data sharing among communities of interest.
While putting business systems on the Internet offers potentially unlimited opportunities for increasing efficiency and reducing cost, it also offers potentially unlimited risk. The Internet provides much greater access to data, and to more valuable data, not only to legitimate users, but also to hackers, disgruntled employees, criminals, and corporate spies.
One of the chief e-business benefits of the Internet is disintermediation. The intermediate information processing steps that employees typically perform in traditional businesses, such as typing in an order received over the phone or by mail, are removed from the e-business process. Users who are not employees and are thus outside the traditional corporate boundary (including customers, suppliers, and partners) can have direct and immediate online access to business information that pertains to them.
In a traditional office environment, any access to sensitive business information is through employees. Although employees are not always reliable, at least they are known, their access to sensitive data is limited by their job function, and access is enforced by physical and procedural controls. Employees who pass sensitive information outside the company contrary to policy may be subject to disciplinary action. The threat of punishment thus helps prevent unauthorized access.
Making business information accessible by means of the Internet vastly increases the number of users who may be able to access that information. When business is moved to the Internet, the environment is drastically changed. Companies may know little or nothing about the users (including, in many cases, employees) who are accessing their systems. Even if they know who their users are, it may be very difficult for companies to deter users from accessing information contrary to company policy. It is therefore important that companies manage access to sensitive information, and prevent unauthorized access to that information before it occurs.
E-business relies not only on making business information accessible outside the traditional company, it also depends on making the best, most up-to-date information available to users when they need it. For example, companies can streamline their operations and reduce overhead by allowing suppliers to have direct access to consolidated order information. This allows companies to reduce inventory by obtaining exactly what they need from suppliers when they need it. Companies can also take advantage of new pricing technology, such as online competitive bidding by means of exchanges, to obtain the best price from suppliers, or offer the best price to consumers.
Streamlining information flow through the business system allows users to obtain better information from the system. In the past, data from external partners, suppliers, or customers was often entered into the system through inefficient mechanisms that were prone to error and delay. For example, many companies accepted the bulk of their orders by phone, letter, or fax, and this information was typed in by clerks or sales people. Even when electronic data interchange mechanisms existed, they were typically proprietary and difficult to integrate with companies' internal data infrastructure. Now, businesses that allow other businesses and consumers to submit and receive business information directly through the Internet can expect to get more timely, accurate, and valuable information, at less expense than if traditional data channels were used.
Formerly, when information was entered into a business system, it was often compartmentalized. Information maintained by each internal department, such as sales, manufacturing, distribution, and finance, was kept separate, and was often processed by physically separate and incompatible databases and applications--so-called "islands of information". This prevented businesses from taking full advantage of the information they already had, since it was difficult for different departments to exchange information when it was needed, or for executives to determine the latest and most accurate status of the business. Companies have found that linking islands of information and consolidating them where possible, allows users to obtain better information, and to get more benefit from that information. This makes the information more valuable.
Improving the value of data available to legitimate users generally improves its value to intruders as well. This increases the potential rewards to be gained from unauthorized access to that data, and the potential damage that can be done to the business if the data were corrupted. In other words, the more effective an e-business system is, the greater the need to protect it against unauthorized access.
The sheer size of the user communities that can access business systems by way of the Internet not only increases the risk to those systems, but also constrains the solutions that can be deployed to address that risk. The Internet creates challenges in terms of scalability of security mechanisms, management of those mechanisms, and the need to make them standard and interoperable.
Security mechanisms for Internet-enabled systems must support much larger communities of users than systems that are not Internet-enabled. Whereas the largest traditional enterprise systems typically supported thousands of users, many Internet-enabled systems have millions of users.
Traditional mechanisms for identifying users and managing their access, such as granting each user an account and password on each system she accesses, may not be practical in an Internet environment. It rapidly becomes too difficult and expensive for system administrators to manage separate accounts for each user on every system.
Unlike traditional enterprise systems, where a company owns and controls all components of the system, Internet-enabled e-business systems must exchange data with systems owned and controlled by others: by customers, suppliers, partners, and so on. Security mechanisms deployed in e-business systems must therefore be standards-based, flexible, and interoperable, to ensure that they work with others' systems. They must support thin clients, and work in multitier architectures.
The principal security challenge of hosting is keeping data from different hosted user communities separate. The simplest way of doing this is to create physically separate systems for each hosted community. The disadvantage of this approach is that it requires a separate computer, with separately installed, managed, and configured software, for each hosted user community. This provides little in the way of economies of scale to a hosting company.
Several factors can greatly reduce costs to hosting service providers. These factors include mechanisms that allow multiple user communities to share a single hardware and software instance; mechanisms that separate data for different user communities; and ways to provide a single administrative interface for the hosting provider.
Exchanges have requirements for both data separation and data sharing. For example, an exchange may ensure that a supplier's bid remains unviewable by other suppliers, yet allow all bids to be evaluated by the entity requesting the bid. Furthermore, exchanges may also support communities of interest in which groups of organizations can share data selectively, or work together to provide such things as joint bids.
The integrity and privacy of data are at risk from unauthorized users, external sources listening in on the network, and internal users giving away the store. This section explains the risky situations and potential attacks that could compromise your data.
Privacy of communications is essential to ensure that data cannot be modified or viewed in transit. Distributed environments bring with them the possibility that a malicious third party can perpetrate a computer crime by tampering with data as it moves between sites.
In a data modification attack, an unauthorized party on the network intercepts data in transit and changes parts of that data before retransmitting it. An example of this is changing the dollar amount of a banking transaction from $100 to $10,000.
In a replay attack, an entire set of valid data is repeatedly interjected onto the network. An example would be to repeat, one thousand times, a valid $100 bank account transfer transaction.
Data must be stored and transmitted securely, so that information such as credit card numbers cannot be stolen.
Over the Internet and in Wide Area Network (WAN) environments, both public carriers and private network owners often route portions of their network through insecure land lines, extremely vulnerable microwave and satellite links, or a number of servers. This situation leaves valuable data open to view by any interested party. In Local Area Network (LAN) environments within a building or campus, insiders with access to the physical wiring can potentially view data not intended for them. Network sniffers can easily be installed to eavesdrop on network traffic. Packet sniffers can be designed to find and steal user names and passwords.
You need to know your users. In a distributed environment, it becomes more feasible for a user to falsify an identity to gain access to sensitive and important information. How can you be sure that user Pat connecting to Server A from Client B really is user Pat?
In addition, malefactors can hijack connections. How can you be sure that Client B and Server A are what they claim to be? A transaction that should go from the Personnel system on Server A to the Payroll system on Server B could be intercepted in transit and routed instead to a terminal masquerading as Server B.
Identity theft is becoming one of the greatest threats to individuals in the Internet environment. Criminals attempt to steal users' credit card numbers, and then make purchases against the accounts. Or they steal other personal data, such as checking account numbers and driver's license numbers, and set up bogus credit accounts in someone else's name.
Nonrepudiation is another identity concern: how can a person's digital signature be protected? If hackers steal someone's digital signature, that person may be held responsible for any actions performed using their private signing key.
In large systems, users must remember multiple passwords for the different applications and services that they use. For example, a developer can have access to a development application on a workstation, a PC for sending e-mail, and several computers or intranet sites for testing, reporting bugs, and managing configurations.
Users typically respond to the problem of managing multiple passwords in several ways:
All of these strategies compromise password secrecy and service availability. Moreover, administration of multiple user accounts and passwords is complex, time-consuming, and expensive.
The database may contain confidential tables, or confidential columns in a table, which should not be available indiscriminately to all users authorized to access the database. It should be possible to protect data on a column level.
Certain data rows may contain confidential information that should not be available indiscriminately to users authorized to access the table.
You need granular access control--a way to enforce confidentiality on the data itself. For example, in a shared environment businesses should only have access to their own data; customers should only be able to see their own orders. If the necessary compartmentalization is enforced upon the data, rather than added by the application, then it cannot be bypassed by users.
Systems must therefore be flexible: able to support different security policies depending on whether you are dealing with customers or employees. For example, you may require stronger authentication for employees (who can see more data) than you do for customers. Or, you may allow employees to see all customer records, while customers can only see their own records.
If the system administrator is unable to track users' activities, then users cannot be held responsible for their actions. There must be some reliable way to monitor who is performing what operations on the data.
Systems must often support thousands of users, or hundreds of thousands of users: thus they must be scalable. In such large-scale environments, the burden of managing user accounts and passwords makes your system vulnerable to error and attack. You need to know who the user really is--across all tiers of the application--to have reliable security.
This problem becomes particularly complex in multitier systems. Here, and in most packaged applications, the typical security model is that of One Big Application User. The user connects to the application, and the application (or application server) logs on and provides complete access for everyone, with no auditing and unlimited privileges. This model places your data at risk--especially in the Internet, where your Web server or application server depends upon a firewall. Firewalls are commonly vulnerable to break-ins.
Administration of hundreds of thousands of users is difficult enough on a single system. This burden is compounded when security must be administered on multiple systems.
To meet the challenges of scale in security administration, you should be able to centrally manage users and privileges across multiple applications and databases by using a directory based on industry standards. This can reduce system management costs and increase business efficiency.
Further, creating and building separate databases for multiple application subscribers is not a cost-efficient model for an application service provider. While technically possible, the separate database model would quickly become unmanageable. To be successful, a single application installation should be able to host multiple companies--and be administered centrally.
Table 1-3 relates security risks to the technologies that address them, and to the corresponding Oracle products.
Complex data security systems require a team of people to ensure security at a particular site. Table 1-4 introduces the types of administrators who may be involved.