| Oracle® Database Advanced Security Administrator's Guide 10g Release 2 (10.2) Part Number B14268-01 |
|
|
View PDF |
| Oracle® Database Advanced Security Administrator's Guide 10g Release 2 (10.2) Part Number B14268-01 |
|
|
View PDF |
This chapter describes how to configure multiple authentication methods under Oracle Advanced Security, and how to use conventional user name and password authentication, even if you have configured another authentication method. This also chapter describes how to configure your network so that Oracle clients can use a specific authentication method and Oracle servers can accept any method specified.
This chapter contains the following topics:
To connect to an Oracle database server using a user name and password when an Oracle Advanced Security authentication method has been configured, disable the external authentication (Refer to "Disabling Oracle Advanced Security Authentication" ).
With the external authentication disabled, a user can connect to a database using the following format:
% sqlplus username/password@net_service_name
For example:
% sqlplus scott/tiger@emp
|
Note: You can configure multiple authentication methods, including both externally authenticated users and password authenticated users, on a single database. |
Use Oracle Net Manager to disable authentication methods (Refer to "Starting Oracle Net Manager"):
Navigate to the Oracle Advanced Security profile. Refer to "Navigating to the Oracle Advanced Security Profile". The Oracle Advanced Security tabbed window is displayed as shown in Figure 10-1.
Figure 10-1 Oracle Advanced Security Authentication Window
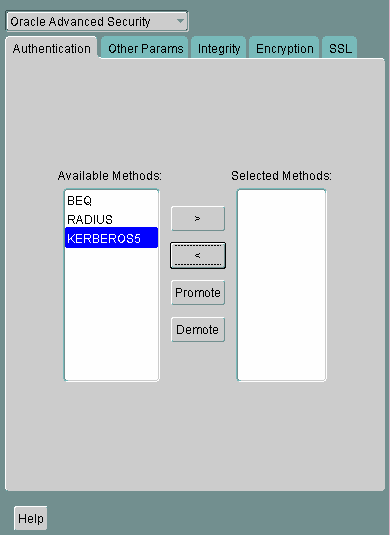
Click the Authentication tab.
Sequentially move all authentication methods from the Selected Method list to the Available Methods list by selecting a method and choosing the left arrow [<].
Select File, then Save Network Configuration.
The sqlnet.ora file is updated with the following entry:
SQLNET.AUTHENTICATION_SERVICES = (NONE)
Many networks use more than one authentication method on a single security server. Accordingly, Oracle Advanced Security lets you configure your network so that Oracle clients can use a specific authentication method, and Oracle database servers can accept any method specified.
You can set up multiple authentication methods on both client and server systems either by using Oracle Net Manager, or by using any text editor to modify the sqlnet.ora file.
Use Oracle Net Manager to add authentication methods to both clients and servers (Refer to "Starting Oracle Net Manager")
Following steps describe how to configure Multiple authentication Methods.
Navigate to the Oracle Advanced Security profile. Refer to "Navigating to the Oracle Advanced Security Profile". The Oracle Advanced Security tabbed window is displayed as shown in Figure 10-1.
Click the Authentication tab.
Select a method listed in the Available Methods list.
Sequentially move selected methods to the Selected Methods list by clicking the right arrow (>).
Arrange the selected methods in order of desired use. To do this, select a method in the Selected Methods list, and select Promote or Demote to position it in the list.
Select File, then Save Network Configuration.
The sqlnet.ora file is updated with the following entry, listing the selected authentication methods:
SQLNET.AUTHENTICATION_SERVICES = (RADIUS|KERBEROS5)
|
Note: SecurID functionality is available through RADIUS; RADIUS support is built into the RSA ACE/Server. |
This section describes the parameters you must set to configure Oracle Database for network authentication, using the following tasks:
Setting the SQLNET.AUTHENTICATION_SERVICES Parameter in sqlnet.ora
Setting OS_AUTHENT_PREFIX to a Null Value
|
See Also:
|
The following parameter must be set in the sqlnet.ora file for all clients and servers to enable each to use a supported authentication method:
SQLNET.AUTHENTICATION_SERVICES=(oracle_authentication_method)
For example, for all clients and servers using Kerberos authentication, the sqlnet.ora parameter must be set as follows:
SQLNET.AUTHENTICATION_SERVICES=(KERBEROS5)
To verify that REMOVE_OS_AUTHENT is not set to TRUE, add the following parameter to the initialization file, in each database instance when you configure the authentication method:
REMOTE_OS_AUTHENT=FALSE
|
Caution: SettingREMOTE_OS_AUTHENT to TRUE can cause a security exposure, because it lets someone using a non-secure protocol, such as TCP, perform an operating system-authorized login (formerly referred to as an OPS$ login). |
|
Note: In addition to setting theREMOTE_OS_AUTHENT initialization parameter file to FALSE, you should issue the startup command with a PFILE option. This ensures that the parameters from your initSID.ora are used. |
If REMOTE_OS_AUTHENT is set to FALSE, and the server cannot support any of the authentication methods requested by the client, then the authentication service negotiation fails and the connection terminates.
If the parameter is set as follows in the sqlnet.ora file on either the client or server, the database attempts to use the supplied user name and password to login the user:
SQLNET.AUTHENTICATION_SERVICES=(NONE)
If REMOTE_OS_AUTHENT is set to FALSE, however, the connection fails.
Authentication service-based user names can be long, and Oracle user names are limited to 30 characters. Oracle strongly recommends that you enter a null value for the OS_AUTHENT_PREFIX parameter in the initialization file used for the database instance as follows:
OS_AUTHENT_PREFIX=""
|
Note: The default value forOS_AUTHENT_PREFIX is OPS$; however, you can set it to any string. |
|
Attention: If a database already has theOS_AUTHENT_PREFIX set to a value other than NULL (" "), do not change it, because it can inhibit previously created, externally identified users from connecting to the Oracle server. |
To create a user, launch SQL*Plus and enter the following:
SQL> CREATE USER os_authent_prefix username IDENTIFIED EXTERNALLY;
When OS_AUTHENT_PREFIX is set to a null value (" "), enter the following to create the user king:
SQL> CREATE USER king IDENTIFIED EXTERNALLY;
The advantage of creating a user in this way is that the administrator no longer needs to maintain different user names for externally identified users. This is true for all supported authentication methods.